How to earn more than 27 ETH in less than 4 hours launching a $PSYOP honeypot
We will analyze how a scammer managed to steal more than $50,000 in a few hours by launching a honeypot around the ben.eth token and spoofing him transactions.
These weeks we have seen how memecoins became again the meta of the ecosystem and everyone was trying to find the next $PEPE to multiply their money.
A few days ago ben.eth announced that he was going to launch a token called $PSYOP and to participate in the pre-sale of the token you had to send ether to his wallet.
Scammers were quick to see the opportunity to make money and started to deploy fake PSYOP tokens, the case we are going to analyze is just one of the dozens that have been created.
What is a honeypot?
Before I start I will explain when a token in ethereum can be called a honeypot, basically it usually refers to a scam in which the token or contract appears to be legitimate and profitable, but in reality, it is designed to trick users into participating and then steal their funds.
Some of the techniques they use are:
Impossible to sell tokens
High returns promised
Lack of transparency
Quick pump
Social media manipulation
Lack of liquidity
The $PSYOP deployment
It all starts when the scammer deploys the contract in this transaction:
Let's take a quick look at the code that is automatically executed when the contract is deployed.
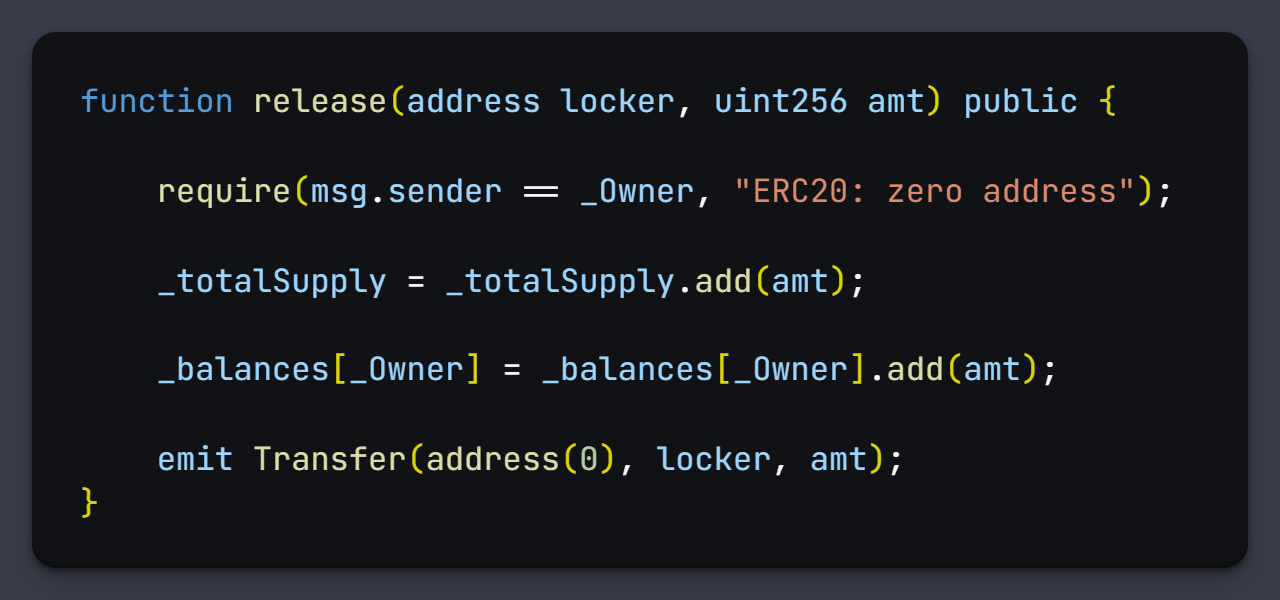
First it assigns to the name and symbol the value PSYOP, then it assigns an initial supply of 210 billion, so far nothing out of the ordinary, the interesting part comes when we see a variable called team with the address of ben.eth and the call to the release function.
This function can only be used by the owner of the contract and what it does is to add to the total supply and to the owner's balance the indicated amount, but it emits a spoof mint event from the indicated address.
Etherscan works with the events of the smart contracts and in this way is tricking the site to simulate that ben received that amount of tokens.
The Uniswap pool creation
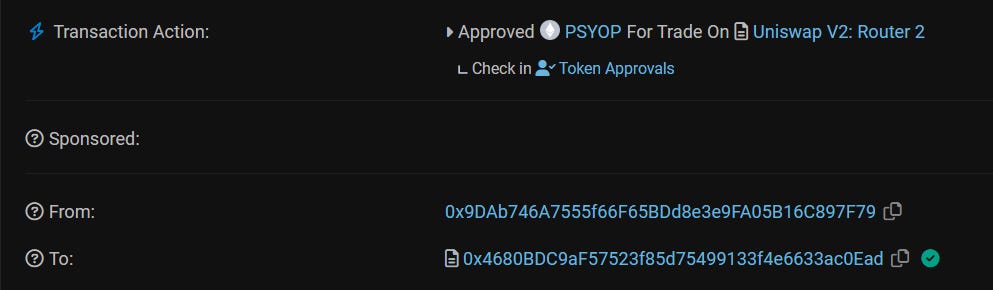
The scammer approves PSYOP for trade on Uniswap
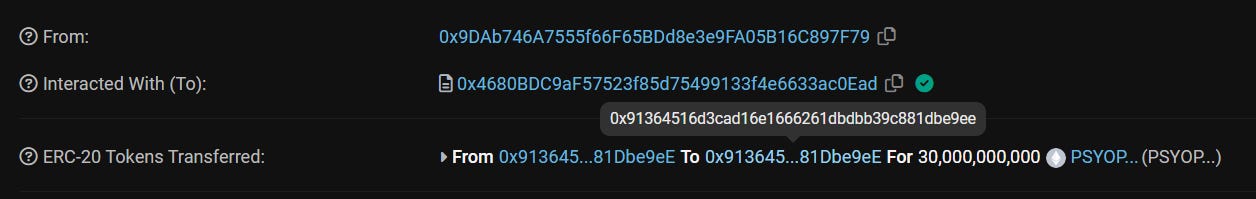
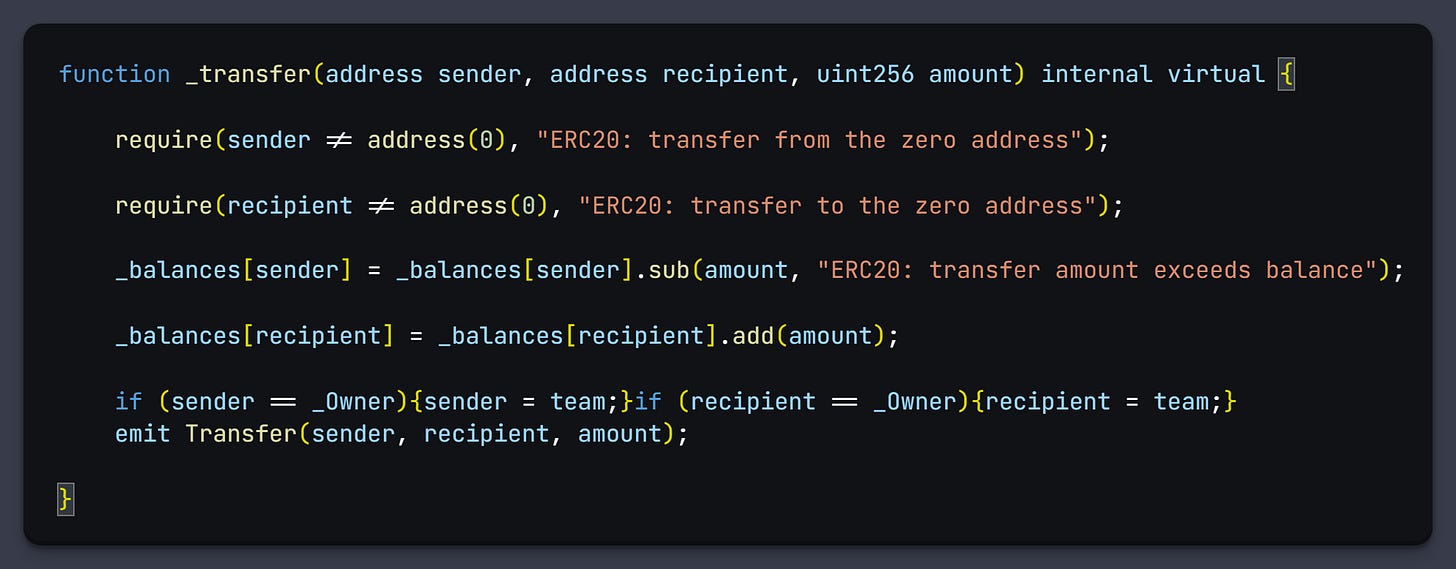
It then uses a modified version of transfer to pretend that ben.eth has transferred 30 billion to itself, the transfer function works normally, but if it detects that the owner is the one transferring the tokens it emits a ben.eth spoofing event.
The scammer adds 100 ETH of liquidity to the uniswap pool and the modified transfer acts again and pretends that Ben was the one who made the transaction
Imagine looking at etherscan and seeing that ben has created the Uniswap pool, many unwary people will run to buy the token on uniswap.
Presale airdrop to selected people
Now the scammer uses the presaleAirdrop function to pretend a $PSYOP airdrop to a selected list of people who sent money in the ben.eth presale.
Yes, pretend, those fake tokens were never actually sent
As I mentioned before, these transactions appear in etherscan as if ben had performed them
People start buying PSYOP at Uniswap
After that, the purchase transactions started coming in from people who did not want to lose the opportunity to multiply their money, or so they thought.
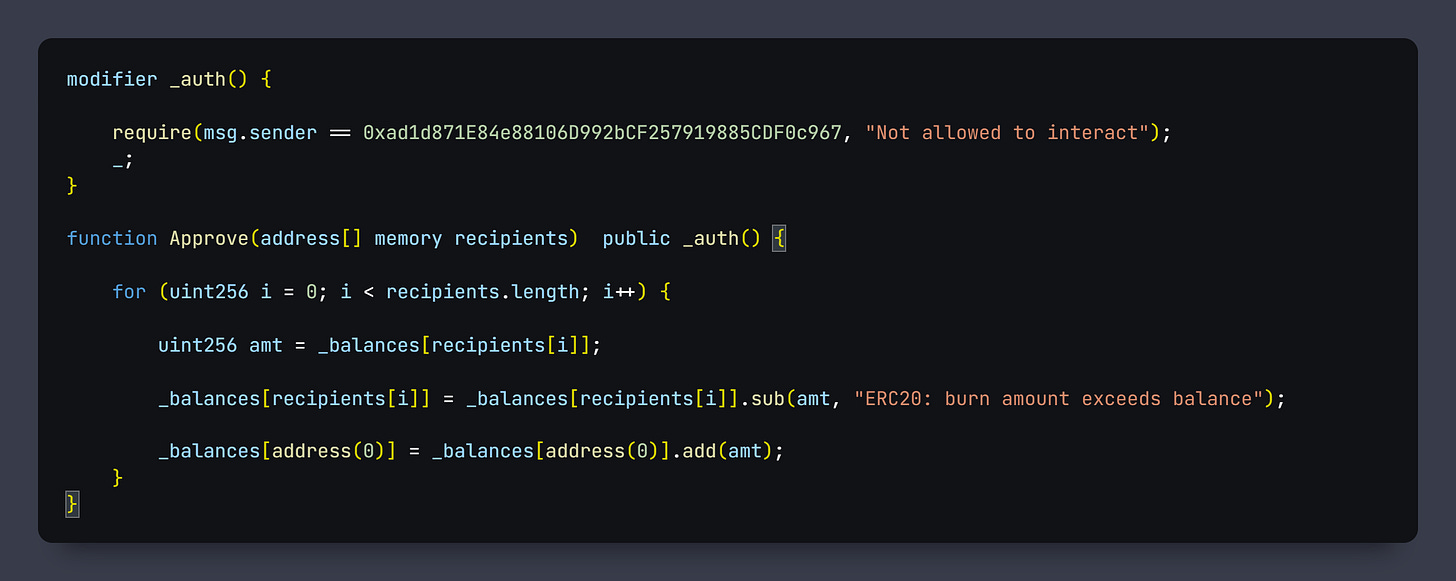
In the meantime the scammer only had to write down the addresses of the buyers to send a transaction that would burn all their tokens.
In addition, the name of the function he uses is Approve, a transaction that only he can use, so that no one suspects those transactions.
The game ends
The final moment came, where the hacker apparently got bored of burning tokens and decided to take out all the liquidity.
The scammer ended up earning more than 27 ether in less than 4 hours, ready to deploy another fake contract and continue scamming…
If you liked the article I would like to thank you for sharing and supporting the promotional tweet: